Automated provisioning for Fiserv
In today's fast-paced digital landscape, efficient user management and secure access control are paramount, which is why organizations are turning to solutions like Fiserv SCIM (System for Cross-domain Identity Management) to streamline user provisioning, authentication, and authorization processes.
Regrettably, most business applications are incompatible with the SCIM specification, which automates user onboarding and offboarding from applications. These "nonfederated" applications, in the cloud and on-premises, are a growing area of risk for businesses.
The good news is that Cerby seamlessly integrates all your applications with your identity provider, regardless of whether they align with the SCIM specification.
In this informative guide, we'll delve into the specifics of Fiserv software, explore its historical evolution, and illuminate its advantages.
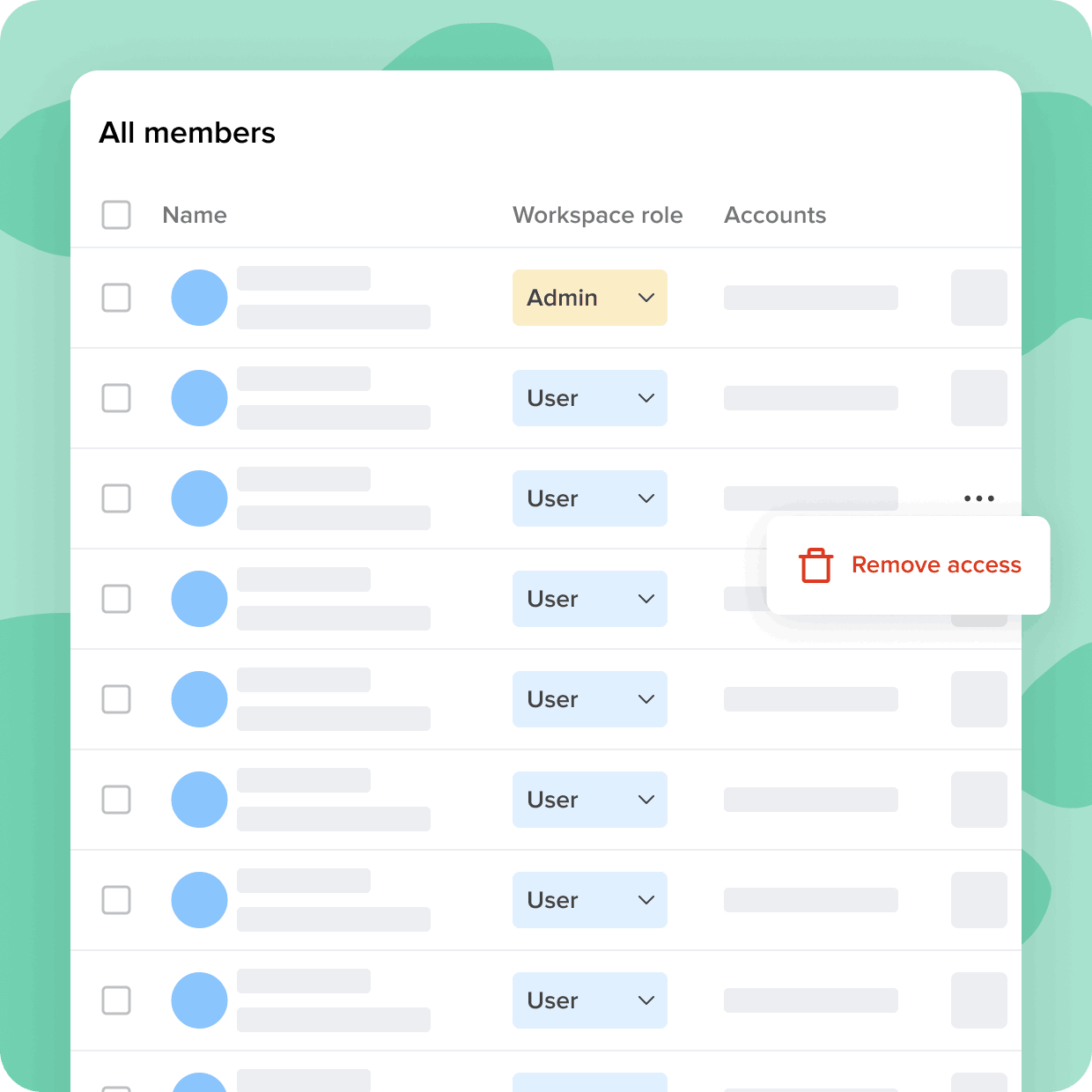
Automate onboarding and offboarding to any app
Not all apps are created equal. Some come with security gaps and complexities that can hinder user adoption and put sensitive data at risk. With Cerby, you can ensure secure and seamless access to all your applications, regardless of their support for specifications like SCIM.
With Cerby you can

Automate offboarding
Cerby's RPA technology automates offboarding from non-SCIM supporting applications, ensuring that access is revoked promptly and accurately, reducing the risk of unauthorized access to sensitive information.

Centralize management
Cerby provides a bridge between your identity provider and applications that don't support SCIM, giving you a centralized dashboard to manage offboarding across all applications, eliminating the need for manual processes and reducing the risk of errors.
Offboard with confidence
Cerby's audit trail provides detailed information on offboarding activities, including the time and date of each action, providing an additional layer of security and compliance for organizations.
Offboard like a boss with Cerby
Automated provisioning for Fiserv
Fiserv provisioning and deprovisioning play crucial roles in managing user access and security in the context of digital wallets and financial services. Provisioning is the process of granting authorized users access to the required resources, while deprovisioning involves revoking access rights when they are no longer needed. Establishing a comprehensive provisioning and deprovisioning policy is of utmost importance for organizations to maintain a secure and efficient environment.
Having a user access provisioning policy ensures that the right individuals have access to the appropriate resources within a financial services organization. A user access provisioning policy should outline the rules, guidelines, and procedures for granting and managing user access to digital wallets and related systems.
By enforcing a well-defined policy, organizations can maintain control over user access and minimize the risk of unauthorized access or misuse of sensitive financial information. Maintaining a robust policy also helps ensure compliance with industry regulations and data protection standards.
Deprovisioning, on the other hand, is a crucial aspect of user access management that focuses on removing or revoking user privileges and rights when they are deemed unnecessary or no longer authorized. By doing so, organizations can safeguard sensitive information and mitigate the risk of potential security breaches.
Deprovisioning should be conducted in a timely manner to minimize the window of vulnerability. When an employee leaves an organization or changes roles, their access privileges should be promptly removed to prevent unauthorized access to confidential data. Failing to deprovision accounts in a timely manner could lead to unauthorized access to sensitive data, intellectual property theft, or misuse of resources.
Setting up provisioning and deprovisioning
Provisioning and deprovisioning controls are crucial elements of an effective user access management strategy. Provisioning involves several steps, starting with the identification of user roles and privileges required to perform specific tasks. Once these roles are established, administrators can assign them to individual users based on their responsibilities and job functions.
To set up provisioning and deprovisioning effectively, organizations need to establish clear workflows. Establishing workflows typically begins with defining the roles and responsibilities of different stakeholders, such as administrators, managers, and human resources personnel.
Additionally, organizations should implement robust identity and access management systems that facilitate the automation of provisioning and deprovisioning processes. These systems should include features such as user lifecycle management, access request workflows, and audit logs for monitoring and compliance purposes.
Fiserv user access management
Fiserv user access management plays a vital role in ensuring privacy and security within financial services organizations. Effective management of Fiserv access credentials and implementation of robust security measures are crucial for safeguarding sensitive information and mitigating cybersecurity risks.
Fiserv user access management involves the control and administration of user credentials and privileges within the digital wallet and financial service systems. It encompasses processes such as:
- User provisioning
- Authentication
- Authorization
- User deprovisioning
Effective user access management helps maintain the confidentiality, integrity, and availability of sensitive financial data, all of which are essential for protecting customer privacy and ensuring a secure environment.
Privacy
Privacy is a critical aspect of user access management. It’s very important for organizations to adhere to data protection regulations and maintain customer confidentiality. By implementing stringent access controls, such as multi-factor authentication (MFA) and role-based access control, Fiserv users can ensure that only authorized individuals can access specific resources. Taking the appropriate privacy precautions can help prevent unauthorized access, data breaches, or identity theft, thus safeguarding customer privacy.
Security
Security is another crucial aspect of Fiserv user access management. Cybersecurity threats, such as phishing attacks, malware, and unauthorized access attempts are persistent risks in the financial services industry. Effective user access management minimizes these risks. By employing robust security measures, such as strong password policies, encryption, and regular security audits, Fiserv users can improve user protection and reduce the chances of malicious actors gaining access to sensitive information.
Additionally, user deprovisioning (the process of revoking access rights when no longer required) ensures that former employees or individuals who no longer need access cannot compromise sensitive information.
Risk management
Cybersecurity and risk management are both important parts of Fiserv user access management. A comprehensive user access management strategy reduces the potential for security breaches, financial fraud, and reputational damage. It also helps organizations identify and mitigate security vulnerabilities, monitor access activities, and detect anomalous behavior.
Additionally, by implementing push provisioning mechanisms, where access privileges are automatically provisioned based on predefined rules and policies, organizations can minimize manual errors and ensure a consistent and controlled access provisioning process.
Fiserv user access management is integral to privacy and security within financial services organizations. By implementing robust security measures, adhering to data protection regulations, and employing effective user access management practices, organizations can enhance their cybersecurity posture and mitigate potential risks, ultimately safeguarding their reputation and maintaining customer trust.
Authentication and provisioning
Authentication and provisioning are critical components of user access management within the Fiserv ecosystem. They play a pivotal role in verifying user identities, granting appropriate access privileges, and mitigating user access risks.
Fiserv authentication is the process of verifying the identity of a user before granting access to the Fiserv platform. It ensures that only authorized individuals can access sensitive financial information and perform relevant transactions.
Fiserv authentication methods
Fiserv offers various authentication mechanisms, including Fiserv MFA, which requires users to provide multiple pieces of evidence to validate their identity. MFA significantly enhances security by combining something the user knows (e.g., a password), something they have (e.g., a mobile device), or something they are (e.g., a fingerprint).
Fiserv provisioning
Fiserv provisioning refers to the process of granting and managing user access privileges within Fiserv solutions. User provisioning involves defining user roles, assigning appropriate access levels, and ensuring that users have access to the resources necessary to fulfill their job responsibilities. A well-defined provisioning process reduces the risk of unauthorized access and helps organizations maintain control over user access.
Businesses should maintain authentication and provisioning policies that outline the procedures, guidelines, and standards for effective user authentication, access provisioning, and access revocation. A successful authentication and provisioning policy should address aspects such as:
- Password complexity
- MFA requirements
- User role definitions
- The approval process for granting access privileges
Regularly reviewing and updating these policies in line with evolving security threats and regulatory requirements is crucial.
The role of automation in authentication and provisioning processes
Automation can play a crucial role in streamlining authentication and provisioning processes within Fiserv. By leveraging automation tools and technologies, businesses can efficiently manage user access at scale while minimizing the risk of manual errors. Automation can facilitate user provisioning workflows, including:
- Creation of user accounts
- Assignment of roles and privileges
- Integration with identity management systems
Additionally, automation can enforce MFA requirements, enabling the secure and seamless authentication of users across multiple channels and devices.
Implementing automation can also help organizations promptly respond to user access changes, such as onboarding new employees or revoking access for departing staff. By integrating with human resources systems and leveraging predefined workflows, automation can expedite the provisioning and deprovisioning processes, ensuring that user access is granted or revoked in a timely manner.
Automatic suspension and deprovisioning
Automatic suspension and deprovisioning are important processes within the Fiserv ecosystem that help businesses manage user access efficiently and mitigate security risks. These processes involve the automatic suspension of user accounts and the subsequent deprovisioning of access privileges when certain conditions are met.
Automatic suspension is the process of temporarily disabling user accounts when specific triggering events occur, including:
- Suspicious or anomalous activities
- Failed authentication attempts
- Detection of potential security breaches
By automatically suspending user accounts, businesses can proactively protect sensitive financial information and prevent unauthorized access.
Automatic suspension vs. deprovisioning
Deprovisioning refers to the process of revoking user access privileges when they are no longer needed. This can occur when an employee leaves the organization, changes roles, or no longer requires access to certain resources. Automatic deprovisioning ensures that access rights are promptly removed, minimizing the risk of unauthorized access and potential data breaches.
Benefits of automation
Automation plays a central role in implementing and enforcing automatic suspension and deprovisioning processes within the Fiserv ecosystem. By leveraging automation tools and technologies, businesses can streamline these processes, reduce manual efforts, and enhance security. Automated systems can:
- Continuously monitor user activities
- Detect suspicious behavior or policy violations
- Trigger automatic suspension when necessary
- Automate the deprovisioning process based on predefined rules and workflows
Implementing automation can also help organizations promptly respond to user access changes and ensure compliance. When an employee leaves the organization, for example, automation can facilitate the deprovisioning process by automatically revoking access privileges, disabling user accounts, and updating access control systems. This eliminates the risk of human error and ensures that user access is revoked in a timely and consistent manner.
Automation also enables businesses to generate audit logs and record automatic suspension and deprovisioning activities. These logs are essential for monitoring and compliance purposes, providing a trail of actions taken and facilitating investigations or audits when required.


